RISKS and challenges of IoT and its cybersecurity
物联网及其网络安全的风险和挑战
物联网 With the rapid innovation and advancement in technology, it has brought supreme revolutionization in human civilization. Technology..
TABLE OF CONTENTS
Abstract…………………………………………………………………………………2
- Introduction…………………………………………………………………………….3
- Facilitations Provided by IOT…………………………………………………………3
- Computerization and Control……………………………………………………….3
- Provision of Information…………………………………………………………….3
- Monitoring and Updates…………………………………………………………......4
- Communication………………………………………………………………………4
- Advancement in Tasks……………………………………………………………….4
- Time efficiency……………………………………………………………………….5
- Accentuating Growth of Cybersecurity Issues relating to IoT Technology………....5
- Ultimate Challenges and Security Threats Proposed by IoT Technology……….…..6
- Outmoded Software and Hardware…………………………………………………...6
- Utilization of Feeble and Automatic Credentials ……………………………….…...7
- Difficulty in Analyzing if the IoT Appliance is Affected………………….………....7
- Protection of Data and Resources……………………………………………….……7
- Malware and Crypto ware………………………………………………………….…8
- Impact of IoT Security Threats on various Industries…………………………….…..8
- Impact on Business and Marketing Sector………………………………………….…8
- Impact on Manufacturing Industries……………………………………………….….9
- Impact on Healthcare Industries………………………………………………………9
- Prevention from IoT Security threats and Risks………………………………………9
- Conclusion………………………………………………………………………………10
- References ………………………………………………………………………………11
译文:目录 物联网
摘要…………………………………………………………………………………………2
引言…………………………………………………………………………………….3
物联网提供的便利………………………………………………………………3
计算机化和控制……………………………………………………………….3
信息的提供…………………………………………………………………….3
监测和更新……………………………………………………………………4
通讯………………………………………………………………………………4
任务进展…………………………………………………………………….4
时间效率……………………………………………………………………………….5
与物联网技术相关的网络安全问题日益严重…………..5
物联网技术提出的终极挑战和安全威胁…………...6
过时的软件和硬件………………………………………………………………6
弱和自动凭证的利用…………………………………………..7
难以分析 IoT 设备是否受到影响……………………………………..7
数据和资源的保护………………………………………………………………7
恶意软件和加密软件……………………………………………………………………8
物联网安全威胁对各行各业的影响………………………………...8
对商业和营销部门的影响……………………………………………………8
对制造业的影响…………………………………………………………..9
对医疗保健行业的影响………………………………………………………………9
物联网安全威胁和风险防范……………………………………9
结论……………………………………………………………………………………10
参考文献…………………………………………………………………………………………11
ABSTRACT
With the rapid innovation and advancement in technology, it has brought supreme revolutionization in human civilization. Technology has facilitated humans in every sector and with the current advancement in the technological sector, it has rewarded mankind with artificial intelligence, robotics, and Internet of Things IoT.
The technology of IoT has allowed people to think more innovatively and has brought ease in the functioning of daily tasks. It has induced productivity in the major sectors such as stock markets, businesses, manufacturing, and production industries, and various other industries, not only that it has made it easier to monitor and keep a check on the work progress of several tasks.
It has improved the working control of operating systems. But with its several facilitations comes the risks and challenges too. There are various risks and security challenges that people observe in the implementation of IoT because as it is entirely connected to various online platforms it has direct access to the internet making it not so secure in its mechanism, as it is still limited by several risks and challenges in its cybersecurity.
译文:抽象的 物联网
随着科技的快速创新和进步,它给人类文明带来了至高无上的革命。技术在各个领域都为人类提供了便利,随着当前技术领域的进步,它以人工智能、机器人技术和物联网物联网来回报人类。
物联网技术使人们能够以更具创新性的方式思考,并为日常任务的运作带来便利。它促进了股票市场、商业、制造和生产行业等主要行业以及其他各个行业的生产力,不仅使监控和检查多项任务的工作进度变得更加容易。
它改进了操作系统的工作控制。但随着它的一些便利化,风险和挑战也随之而来。人们在物联网的实施过程中观察到各种风险和安全挑战,因为它完全连接到各种在线平台,它可以直接访问互联网,因此其机制并不那么安全,因为它仍然受到一些风险和其网络安全方面的挑战。
1. Introduction
The technology of the Internet of Things is fundamentally known to connect various other technological devices and is indicated as the next major revolution in the industrial sector. It has transformed the dimension of the interconnection of various devices. IoT is an augmentation of the prevailing interconnection between humans and technological devices that involves the addition of things that are connected digitally.
IoT devices are used to record and calculate data that can be from various sources such as mobile phones or even stationary, it can also involve the measuring and reporting of complex data from various devices.

Figure 1
译文:1. 简介 物联网
众所周知,物联网技术可以连接各种其他技术设备,并被认为是工业领域的下一次重大革命。 它改变了各种设备互连的维度。 物联网是人类与技术设备之间普遍互连的增强,涉及添加数字连接的事物。
物联网设备用于记录和计算来自各种来源的数据,例如手机甚至固定设备,也可能涉及来自各种设备的复杂数据的测量和报告。
2. Facilitations Provided by IoT
2.1 Computerization and Control
The IoT technology enables the various device to be connected digitally use wireless networks, reduces the mad labor in controlling this device. This provides the opportunity for people to control all the devices digitally and with great efficiency without even getting involved in complex tasks (Fattah et al., 2017).
2.2 Provision of Information

Figure 2
This technology of gazillions of suggestions and informative resources while doing ambiguous tasks or making a complex decision and also helps while evaluating even simpler decisions. The companies have installed this technology to enable their decision-making skills to be used with even more efficacy.
译文:2. 物联网提供的便利 物联网
2.1 计算机化和控制
物联网技术使各种设备通过无线网络进行数字连接,减少了控制该设备的疯狂劳动。 这为人们提供了以数字方式控制所有设备的机会,甚至无需参与复杂的任务(Fattah 等人,2017 年)。
2.2 信息提供
图2
这种在执行模糊任务或做出复杂决策时提供大量建议和信息资源的技术,在评估更简单的决策时也有帮助。 这些公司已经安装了这项技术,以便更有效地使用他们的决策技能。
2.3 Monitoring and Updates
Be it at homes, or even in large organizations with the help of this technology people can monitor and get the information relating to the work progress, causing convenience in their daily tasks.
The technology enables people to get the updates about a certain activity, for example, if a company is running out of supplies, or if at home a particular thing is going finish soon then this technology can keep you updated by its programming (Hwang, Seo, Park, and Park, 2016).
2.4 Communication
The technology provides an interaction or communication between the devices also named as Machine to Machine communication. Due to this technological device can interconnect with each other and this maximizes the overall lucidity with great effectiveness and with fewer chances of any errors.
2.5 Advancement in Tasks
The most substantial advantage of this technology is that it has revolutionized the whole criteria for performing different tasks. It has improved the working horizon for various tasks reducing man labor and has provided them with ease in the tasks. It has reduced the overall working hours for people and every task is completed with great quality through the implementation of this technology (Kim, 2016).
2.6 Time Efficiency
The technology reduces the working hours without compromising the overall performance of the tasks. As technology is a prototype of artificial intelligence that works digitally it reduces saves the time duration while completing the tasks, while optimizing the process.
译文:2.3 监控和更新 物联网
无论是在家中,甚至在大型组织中,借助这项技术,人们都可以监控并获取与工作进度相关的信息,从而为日常工作带来便利。
该技术使人们能够获得有关某项活动的最新信息,例如,如果一家公司的供应用完,或者如果在家中某件事即将完成,那么该技术可以通过其编程让您保持最新状态(Hwang, Seo 、公园和公园,2016 年)。
2.4 沟通
该技术提供设备之间的交互或通信,也称为机器对机器通信。由于这种技术设备可以相互连接,这可以最大限度地提高整体清晰度,并具有很高的效率,并且出现任何错误的机会更少。
2.5 任务推进
这项技术最大的优势在于它彻底改变了执行不同任务的整个标准。它改善了各种任务的工作视野,减少了人工,并为他们提供了轻松完成任务。通过实施这项技术,它减少了人们的整体工作时间,每项任务都以高质量完成(Kim,2016)。
2.6 时间效率
该技术在不影响任务的整体性能的情况下减少了工作时间。由于技术是数字化工作的人工智能原型,因此可以在完成任务和优化流程的同时减少持续时间。
3. Accentuating Growth of Cybersecurity Issues relating to IoT Technology
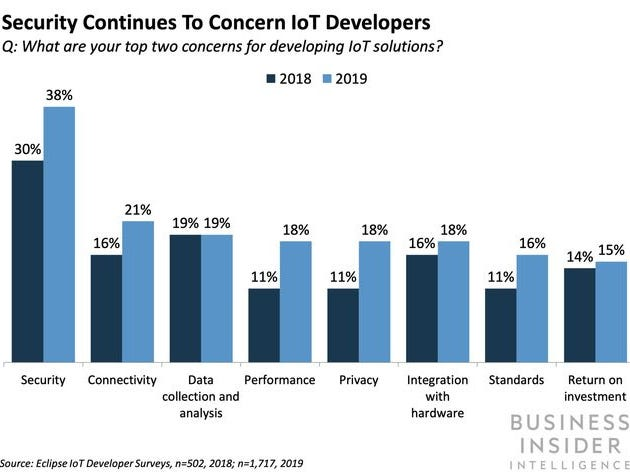
Figure 3
IoT technology has undoubtedly improved various complex tasks and their executions and has cultivated several productive outcomes due to which the implementation of this technology has found to be increased.
It has helped in optimizing the performance of tasks, enabled people to save time and increase efficiency while performing tasks, has increased innovation and productivity, and even has provided cost-efficient methods for the execution of processes. But as with its success factors, various security threats have been introduced in relevance to this technology.
Various threats and risks have been reported by the users and technologists and the number of threats that are encountered by people using this technology is progressing day by day, making it not secure in its working mechanism. As reported by the RFID journal they even implied this technology as an “A Doomsday Scenario Waiting to Unfold”.
The major reason that serves this point is their inexpensiveness, as these devices are cheap, they propose various threats and also because investors don't contribute enough funds to make this technology a little bit more secure.
The devices are quite cheap in their overall manufacturing and retailing procedures and some analysts have even reported that by 2020 the expected devices to be installed throughout the globe adds up to a whopping number of 20 billion, with most of them being low budget expendable artifacts (Jalali, Kaiser, Siegel, and Madnick, 2017).
译文:3. 与物联网技术相关的网络安全问题加剧 物联网
图 3
物联网技术无疑改善了各种复杂的任务及其执行,并产生了一些富有成效的成果,因此发现该技术的实施有所增加。
它帮助优化了任务的性能,使人们能够在执行任务时节省时间并提高效率,提高了创新和生产力,甚至为流程的执行提供了具有成本效益的方法。但是,与其成功因素一样,已经引入了与该技术相关的各种安全威胁。
用户和技术人员报告了各种威胁和风险,使用该技术的人遇到的威胁数量与日俱增,使其工作机制变得不安全。正如 RFID 杂志报道的那样,他们甚至暗示这项技术是“等待展开的世界末日情景”。
支持这一点的主要原因是它们的价格低廉,因为这些设备很便宜,它们提出了各种威胁,还因为投资者没有提供足够的资金来使这项技术更加安全。
这些设备的整体制造和零售程序非常便宜,一些分析家甚至报告说,到 2020 年,预计在全球安装的设备总数将达到 200 亿,其中大部分是低预算的消耗品( Jalali、Kaiser、Siegel 和 Madnick,2017 年)。
4. Ultimate Challenges and Security Threats Proposed by IOT Technology
There are a plethora of security issues and challenges being possessed by the IoT technology, which resultantly makes it a non-secure platform and also increases the problems and challenges for the users. Some of the most prominent security threats offered by the implementation of this technology are as follows.
译文:4. 物联网技术提出的终极挑战和安全威胁 物联网
物联网技术存在大量的安全问题和挑战,导致其成为一个不安全的平台,也增加了用户面临的问题和挑战。 该技术的实施提供的一些最突出的安全威胁如下。
Figure 4
4.1 Outmoded Software and Hardware
The usage of IoT technology has certainly increased and the developers of these devices and technologies are just busy in the production of more and more devices rather than paying heed on the update of the previous models. Hardware and Software of such devices become vulnerable to attack when the hacker finds even the slightest amount of bug or error he plans to attack.
Due to lack of modifications and updates the IoT technology when being excessively used becomes quite outdated which proposes a serious security threat for the users.
- Utilization of Feeble and Automatic Credentials
Most of the developers of this technology are providing the customers with the automatically set credentials such as user name, user id, and login password. This password and Id are initially weak and the hacker just needs to access these things to attack the IoT devices which is easy for them through the brute-force attacks making them unable to enter the programming of the devices without permission from the users.
Some of the developers also don't provide the directives relating to the process of modification, making the user unable to modify his device which also increases the security threat (Rose and Kass, 2017).
4.1 过时的软硬件 物联网
4.3 Difficulty in Analyzing if the IoT Appliance is Affected
As the usage of IoT devices is found to increase every day, with the increase in the devices the developers are unable to keep track of the existing devices and their operations. As an IoT appliance needs to have configuration, apps, programming and other updates for its successful execution sometimes it becomes quite hectic even for the developers to control and manage every single device,
Consequently, some of the devices operate without the supervision and the developer doesn't have the idea whether the device has been hacked or is affected by any virus. Increasing serious security threats (Shackelford, 2018).
4.4 Protection of Data and Resources
In this era where everything is connected and people are excessively using digital and social platforms it becomes really difficult to keep the data with great security, as most of the devices nowadays are connected to the internet and in no time one can access other devices, there is an every prevailing threat of protecting data from unauthorized sources.
The surveillance of data cannot be guaranteed through the usage of these devices which performs through the internet, as such devices can be hacked and after hacking, hackers can certainly leak all the data and then even utilize it for ill purposes causing extreme inconvenience for the users (Tschider, 2018).
4.3 难以分析物联网设备是否受到影响 物联网
随着物联网设备的使用每天都在增加,随着设备的增加,开发人员无法跟踪现有设备及其操作。由于物联网设备需要配置、应用程序、编程和其他更新才能成功执行,有时即使开发人员控制和管理每一个设备也会变得非常忙碌,
因此,一些设备在没有监督的情况下运行,开发人员不知道设备是否已被黑客入侵或受到任何病毒的影响。日益严重的安全威胁(Shackelford,2018 年)。
译文:4.4 数据和资源的保护
在这个万物互联、人们过度使用数字和社交平台的时代,要保证数据的安全性变得非常困难,因为现在大多数设备都连接到互联网,并且很快就可以访问其他设备,是保护数据免受未经授权来源的威胁。
使用这些通过互联网执行的设备无法保证对数据的监控,因为这些设备可能会被黑客入侵,黑客当然可以泄露所有数据,然后甚至将其用于恶意目的,给用户带来极大的不便(齐德,2018 年)。
4.5 Malware and Crypto ware
Figure 5
The IoT technology has enhanced the daily functioning of tasks and at the same time it has also increased the number of threats and security issues in its implementation. With the rapid popularity of IoT applications, it has made cyber-attacks arrangements uncertain.
Many hackers have devised several techniques that enable them to access any information, data, program, and files easily, and with the installation of IoT devices a user may expect the hacking and it can also even unable the user to access his own devices and own data (Armenia et al., 2018).
An example can be drawn here, if a person is using IOT appliance such as a camera with IOT working mechanism that is used by him to record certain private and confidential activities in his office, in case of any hacker attacks on the device then he can even snatch the opportunity from the user to access his information and videos through that camera and can even wrongly access that information and use for his gains.
Manipulation and exploitation of data and information is a serious threat which is undeniably the most negative challenge faced by the utilizers of IoT technology.
译文:4.5 恶意软件和加密软件 物联网
图 5
物联网技术增强了任务的日常功能,同时也增加了其实施中的威胁和安全问题的数量。随着物联网应用的迅速普及,网络攻击的安排变得不确定。
许多黑客设计了多种技术,使他们能够轻松访问任何信息、数据、程序和文件,并且随着物联网设备的安装,用户可能会预料到黑客攻击,甚至无法访问自己的设备和自己的设备。数据(亚美尼亚等人,2018 年)。
这里可以举个例子,如果一个人正在使用物联网设备,例如具有物联网工作机制的相机,他用来记录办公室中的某些私人和机密活动,以防黑客攻击该设备,那么他可以甚至抢夺用户通过该摄像头访问他的信息和视频的机会,甚至可以错误地访问该信息并为他谋取利益。
对数据和信息的操纵和利用是一种严重的威胁,这无疑是物联网技术使用者面临的最不利的挑战。
5. Impact of IoT Security Threats on various Industries
Several industries where the implementation of IoT devices have become excessively famous can face severe damage with the wrong execution of IoT appliances and such a device can even cause extreme catastrophic results in those industries.
5.1 Impact on Business and Marketing Sectors
IoT technology can contribute to a significant amount of threats and challenges in business sectors. With the excessive use of IoT devices that have a lack of modifications and updates and are installed without any configuration, then such devices can be hijacked by any hackers which can lead to the leakage of important data and information and such threats can cause serious damage to the business.
If that data is transferred by the hacker to other competitors then the business owners can even loose their innovative ideas and leverage in the market.
5.2 Impact on Manufacturing Industries
The IoT applications can cause disastrous manufacturing problems in the production and industrial sectors. Though it is non-negotiable the ease that these devices are providing in the industrial sectors with the rapidness in the manufacturing tasks, excess of dependability on these devices for the manufacturing processes can tend to damage supplies and products.
If any of the devices is hijacked or attacked by any virus then such devices might not be able to produce the desired results and this can cause inconvenience (Sorokin, Bondarchuk and Storchak, 2019).
5.3 Impact on Health Care Industries
Health care sectors are greatly facilitated by the artificial intelligence, robotics and IoT technology and huge-scale medical devices and appliances, but in case of a minor flaw in the manufacturing of these devices, or if they are infected with any virus and such devices can cause health hazards to human rounding up to deadliest results in health care sectors.
译文:5. 物联网安全威胁对各个行业的影响 物联网
一些物联网设备的实施变得过分著名的行业可能会因物联网设备的错误执行而面临严重损害,这样的设备甚至可能在这些行业造成极端的灾难性后果。
5.1 对商业和营销部门的影响
物联网技术可以为商业领域带来大量威胁和挑战。随着物联网设备的过度使用,缺乏修改和更新,没有任何配置就安装,然后这些设备可能被任何黑客劫持,导致重要数据和信息的泄漏,这种威胁可能对设备造成严重损害。这生意。
如果黑客将这些数据传输给其他竞争对手,那么企业主甚至可能会失去他们的创新理念和市场影响力。
5.2 对制造业的影响
物联网应用可能会在生产和工业部门造成灾难性的制造问题。尽管这些设备在工业部门中提供的便利性与制造任务的快速性是不容商量的,但制造过程中对这些设备的过度依赖可能会损坏供应和产品。
如果任何设备被任何病毒劫持或攻击,则此类设备可能无法产生预期的结果,从而造成不便(Sorokin、Bondarchuk 和 Storchak,2019 年)。
5.3 对医疗保健行业的影响
人工智能、机器人和物联网技术以及大规模的医疗设备和器具极大地促进了医疗保健行业的发展,但如果这些设备的制造过程中出现小缺陷,或者它们感染了任何病毒,则此类设备可以对人类造成健康危害,导致医疗保健部门最致命的结果。
6. Prevention from IoT Security threats and Risks
To secure data and information from the access of hackers which is the main concern and limitations of the IoT technology implementation certain steps should be followed to increase the security of the systems.
- The whole IoT technology setup should be closely monitored by the developers and the users to increase the competency of the system and also to ensure security. All the appliances should be controlled and managed with great expertise.
- The passwords and the User ID should be distinct and the users should update them now and then to secure the system from the hackers and their access.
- The IoT technology should be updated and modified according to the updates provided by the developers. The IoT devices should be configured with the latest programs and they should be used with a proper protective measure so that no virus could infect the system and this also increases the processing of the system making it more reliable.
- The IoT devices are checked every once in a while, with antivirus software and programs that will detect and remove the virus making the system more competitive and secure for the users.
- Developers and users of IoT technology should always produce a new network for the connection of these devices so that their connection cannot be merged with other networks and thus decreasing the overall performance. So, to avoid that separate networks should be created for interconnecting separate IoT appliances (Aldaej, 2019).
- The developers should closely monitor the activities performed on the IoT technology and should also control the operation and should make sure that the IoT devices are not connected with the digital networks all the time, as this will enable the hackers to attack the system.
译文:6. 防范物联网安全威胁和风险 物联网
为了防止黑客访问数据和信息,这是物联网技术实施的主要问题和限制,应遵循某些步骤来提高系统的安全性。
整个物联网技术设置应由开发人员和用户密切监控,以提高系统的能力并确保安全。所有的电器都应该用丰富的专业知识来控制和管理。
密码和用户 ID 应该是不同的,用户应该不时更新它们以保护系统免受黑客及其访问的侵害。
IoT 技术应根据开发人员提供的更新进行更新和修改。物联网设备应配置最新的程序,并应采取适当的保护措施使用,以免病毒感染系统,这也增加了系统的处理能力,使其更加可靠。
每隔一段时间检查一次物联网设备,使用防病毒软件和程序来检测和清除病毒,从而使系统对用户更具竞争力和安全性。
物联网技术的开发者和用户应该始终为这些设备的连接创建一个新的网络,这样它们的连接就不会与其他网络合并,从而降低整体性能。因此,为避免创建单独的网络来互连单独的物联网设备(Aldaej,2019 年)。
开发人员应密切监视在 IoT 技术上执行的活动,还应控制操作,并应确保 IoT 设备未始终与数字网络连接,因为这将使黑客能够攻击系统。
7. Conclusion
The technology has entirely transformed the working and execution of several tasks being performed by humans and have offered tremendous facilitations and advantages to people in every sector. The Internet of Things has enabled people to efficiently perform several tasks, with great performance, in a short duration.
It has optimized the execution of several tasks. But with its several benefits comes the security threats and disadvantages that it proposes. The security threats and challenges that come from the excessive use of this technology can cause severe catastrophic results that can ruin the working of several industries making it not a reliable technology.
To deal with these issues, several preventative measures should be taken to make the IoT technology more secure for the usage of people.
译文:7. 结论 物联网
该技术彻底改变了人类正在执行的多项任务的工作和执行方式,并为各个领域的人们提供了巨大的便利和优势。 物联网使人们能够在短时间内高效地执行多项任务,并具有出色的性能。
它优化了几个任务的执行。 但伴随着它的几个好处而来的是它提出的安全威胁和缺点。 过度使用这项技术所带来的安全威胁和挑战可能会导致严重的灾难性后果,从而破坏多个行业的运作,使其不再是一项可靠的技术。
为了解决这些问题,应该采取一些预防措施,使物联网技术对人们的使用更加安全。
References
Aldaej, A., 2019. Enhancing Cyber Security in Modern Internet of things (IoT) Using Intrusion Prevention Algorithm for IoT (IPAI). IEEE Access, pp.1-1.
Armenia, S., Ferreira Franco, E., Nonino, F., Spagnoli, E. and Medaglia, C., 2018. Towards the Definition of a Dynamic and Systemic Assessment for Cybersecurity Risks. Systems Research and Behavioral Science, 36(4), pp.404-423.
Fattah, S., Sung, N., Ahn, I., Ryu, M. and Yun, J., 2017. Building IoT Services for Aging in Place Using Standard-Based IoT Platforms and Heterogeneous IoT Products. Sensors, 17(10), p.2311.
Hwang, S., Seo, J., Park, S. and Park, S., 2016. A Survey of the Self-Adaptive IoT Systems and a Compare and Analyze of IoT Using Self-Adaptive Concept. KIPS Transactions on Computer and Communication Systems, 5(1), pp.17-26.
Jalali, M., Kaiser, J., Siegel, M. and Madnick, S., 2017.
The Internet of Things (IoT) Promises New Benefits And Risks: A Systematic Analysis of Adoption Dynamics of IoT Products. SSRN Electronic Journal,.
Kim, W., 2016. The Business Model of IoT Information Sharing Open Market for Promoting IoT Service. Journal of the Korea society of IT services, 15(3), pp.195-209.
Rose, R. and Kass, J., 2017. Mitigating Cybersecurity Risks. CONTINUUM: Lifelong Learning in Neurology, 23(2), pp.553-556.
Shackelford, S., 2018. Smart Factories, Dumb Policy?: Managing Cybersecurity and Data Privacy Risks in the Industrial Internet of Things. SSRN Electronic Journal,.
Sorokin, D., Bondarchuk, A. and Storchak, K., 2019. INDUSTRIAL NETWORK INFRASTRUCTURE IoT & CYBERSECURITY IN USE IoT SOLUTIONS. Telecommunication and information technologies, (4), pp.120-127.
Tschider, C., 2018. Regulating the IoT: Discrimination, Privacy, and Cybersecurity in the Artificial Intelligence Age. SSRN Electronic Journal,.





发表回复
要发表评论,您必须先登录。