CS3550Operation3
cs计算机作业代写 Why do we use uniform Local Binary Pattern (LBP) code? How many uniform LBP codes are there for an 8-bit LBP coding scheme?
1. (a) Cloning forgery detection requires comparing image regions, and gradient-based features are useful tools for that. Give a 1D kernel that can approximately compute second order gradient. Use your 1D kernel on A to compute the two gradient images corresponding to the two dimensions. Also, compute the gradient magnitude image. Use zero-padding when needed. cs计算机作业代写

(b) Why do we use uniform Local Binary Pattern (LBP) code? How many uniform LBP codes are there for an 8-bit LBP coding scheme? Compute the numbers separately for each case. Show your computations. [7]
(c) State a technique you would use to avoid false matches when performing feature matching to detect cloned regions. Be brief. Use mathematical notations whenever possible. [3]
2. (a) Write a Group of Pictures sequence with parameters (7, 3) in terms of the I, P and B frames. Consider a video with this GoP structure. An attacker removes the 6th frame in the first GoP, and re-encodes the video using the original GoP. Show the newly encoded first two GoPs, clearly indicating the frames that have been encoded differently in the new sequence. How will you detect this forgery? [11]
(b) Under what conditions would you fail to detect
(i) splicing forgery
(ii) frame deletion forgery? [6]
(c) Consider the following random variable X which can only take the three values you see. Compute its entropy.
X = {5, 6, 6, 6, 5, 6, 1, 1, 1}
Under what condition the entropy of X would achieve its maximum value and what is that value? Show your computations. [8]
3. (a) Calculate the 2 × 2 DCT coefficient matrix for an image 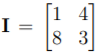 using the 1D DCT bases given by
using the 1D DCT bases given by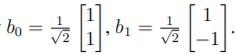 [15]
[15]
(b) Can watermarking using the two least significant bits (LSB) substitution withstand compression attack? Justify your answer. [3]
(c) Which characteristics of sensor pattern noise (SPN) make it suitable for source device identification? Can we use SPN as a watermark for a particular image? Explain. [7]
4. (a) Compute the local luminance and contrast only for the image patch B. Compute the sample correlation coefficient between A and B. Comment on the relationship between A and B. cs计算机作业代写
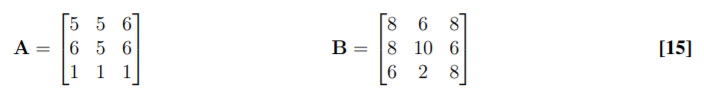
b) What would be the effect on the histogram of an (8-bit, grayscale) image if we set the most significant bitplane to zero? [5]
(c) If you see periodic empty bins in the histogram of DCT coefficients of an image, what could you possibly infer about the image’s authenticity? [5]
5. (a) Match the histogram of M with that of the Ref, assuming both to have 4 graylevels. Your answer should be in the following format: (i) Two tables, one for M and one for Ref, showing the required probability/cumulative values corresponding to the graylevels. (ii) A third table showing the original pixel values in M and their new mappings. (iii) Give the new image matrix.
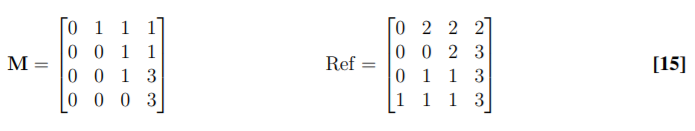
(b) You are given a grayscale image from a surveillance camera to enhance. You see some of its pixels (at random) are completely black and some are completely white. What type of noise is this? If you filter this image with a max kernel (that replaces the center pixel value by the max value within a neighborhood), will it clean the image? What visual effect do you expect to see? [3]
(c) To identify if a device has been used to capture an illegal video, we often need to compare different types of chroma subsampling techniques. Consider the following matrix as a full resolution chroma channel. Subsample C in 4 : 2 : 0 (direct), 4 : 2 : 2 (average) and 4 : 1 : 1 (average) format. Show your computations.


更多代写: HomeWork cs作业 金融代考 postgreSQL代写 IT assignment代写 统计代写 马里兰大学代写




发表回复
要发表评论,您必须先登录。