Final Exam
CS 423/623/723: Network Security Online
计算机final代考 ome wireless networks use white lists consisting of MAC addresses to prevent unauthorized users (wireless stations or hosts) from
[100+30pts]
Instructions (please carefully read these first) 计算机final代考
- The exam consists of
- Problem 1 (with 7 sub-parts) worth 35pts,
- Problem 2 (with 2 sub-parts) worth 20pts,
- Problem 3 (with 3 sub-parts) worth 25pts,
- Problem 4 (with 3 sub-parts) worth 20pts
- Problem 5 worth 30 pts
- There are a total of 9 single-sided sheets. Make sure you have the complete set
- Problem 5 is mandatory for 723 students (so they will be scaled a total of 130 pts). It is optional for 423 and 623 students and can be done for gaining extra 30 points.
- Problems which are more or less objective (i.e., where we do not ask you to explain your answer, why/why not etc.) should be answered objectively and concisely. Write your answers in the space provided
- Problems which are somewhat subjective (i.e., where we want you to explain your reasoning) should be answered in detail showing all steps.
- Your goal is to maximize your score. Spend more time on questions you think you know better than the ones you think you do not. Take a look at the whole exam first, and plan your strategy accordingly.
- You can write your answers in the space allocated – we are providing a word file for you to use.
- This exam is OPEN BOOK.
- No collaboration of any sort is allowed. Violators will, at least, fail the course!
- GOOD LUCK, and THANKS FOR YOUR COOPERATION!
Problem 1 [35pts] (Pre Mid-Term Mix Bag) 计算机final代考
- [2pts] What is the effective level of security provided by triple-DES (with 3 keys)?
- 2112
- 2168
- 256
- 264
- [4pts] Can a MAC scheme (e.g., HMAC or CBC-MAC) provide non-repudiation? Explain your answer.
- [2pts] Which of the following is the correct order in which the encryption, signing and compression operations are performed (at the side of the sender) in PGP:
- Encrypt, Sign, Compress
- Encrypt, Compress, Sign
- Sign, Encrypt, Compress
- Sign, Compress, Encrypt
- [5pts] Describe the SYN Flooding Attack. Describe a defense to this attack.
- [6pts] Following is the output of running “traceroute facebook.com” command on moat.cis.uab.edu.
traceroute to facebook.com (173.252.110.27), 30 hops max, 60 byte packets
1 138.26.64.1 (138.26.64.1) 0.203 ms 0.145 ms 0.131 ms
2 138.26.66.14 (138.26.66.14) 0.754 ms 0.755 ms 0.964 ms
3 138.26.221.33 (138.26.221.33) 1.147 ms 1.142 ms 1.265 ms
4 * * *
5 v832.core1.atl1.he.net (216.218.254.57) 4.010 ms 4.001 ms 3.962 ms
6 198.32.132.104 (198.32.132.104) 19.122 ms 19.181 ms 19.062 ms
7 ae2.bb02.atl1.tfbnw.net (204.15.23.210) 20.391 ms ae1.bb01.atl1.tfbnw.net (74.119.78.214) 18.902 ms 19.321 ms
8 ae11.bb03.frc1.tfbnw.net (31.13.27.120) 27.194 ms 27.193 ms 27.168 ms
9 ae4.dr04.frc1.tfbnw.net (31.13.27.73) 18.811 ms ae1.dr03.frc1.tfbnw.net (31.13.27.76) 18.704 ms ae2.dr04.frc1.tfbnw.net (31.13.27.82) 19.194 ms
10 * * *
11 * * *
12 edge-star-shv-13-frc1.facebook.com (173.252.110.27) 19.055 ms 19.030 ms 18.927 ms
________________________________________________________________________
- [2pts] What does line 3 (including the IP addresses and timestamps) represent?
- [2pts] What does line 10 represent?
- [2pts] What does line 12 (including the hostnames/IP addresses and timestamps) represent?
- [5pts] Explain all the steps needed for an attacker to sniff the data between two hosts on a LAN which uses a hub.
- [11pts] Explain the following functions (show all mathematical computations) underlying the “textbook” RSA encryption scheme:
- [5pts] Key Generation
- [3pts] Encryption
- [3pts] Decryption
Problem 2 [20pts] (SSL/TLS)
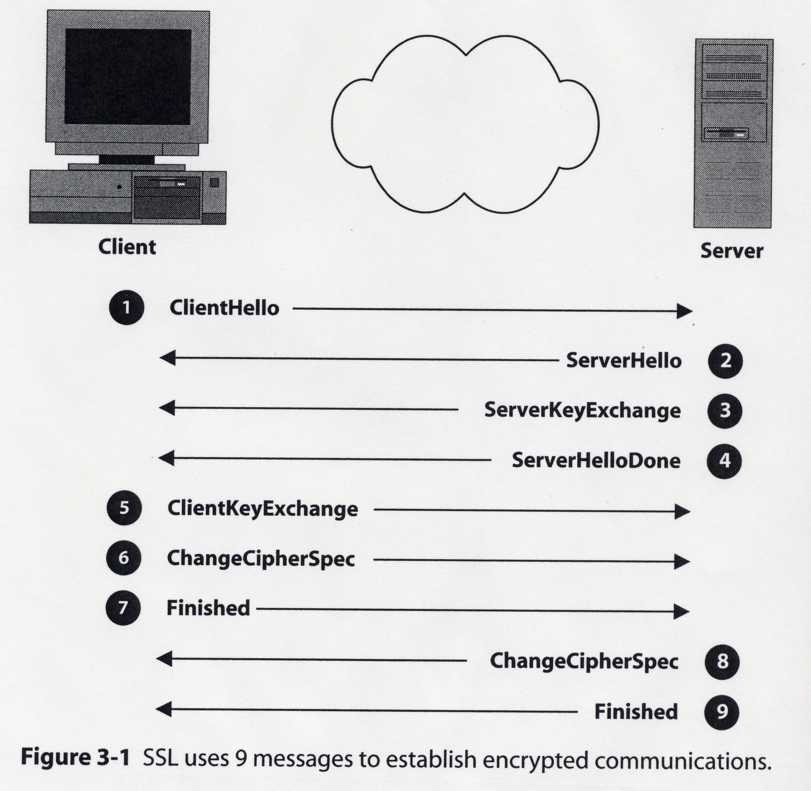
- [15pts] The figure below shows the SSL Handshake Protocol that we studied in the class. What is the purpose of the following messages in this protocol? Explain your answers.
- [5pts] Client Hello and Server Hello ________________________________________
- [5pts] ServerKeyExchange ¬¬¬¬¬¬¬¬¬Check if the CA is trustedEW
- [5pts] Finished
- [5pts] Describe the Heartbleed vulnerability.
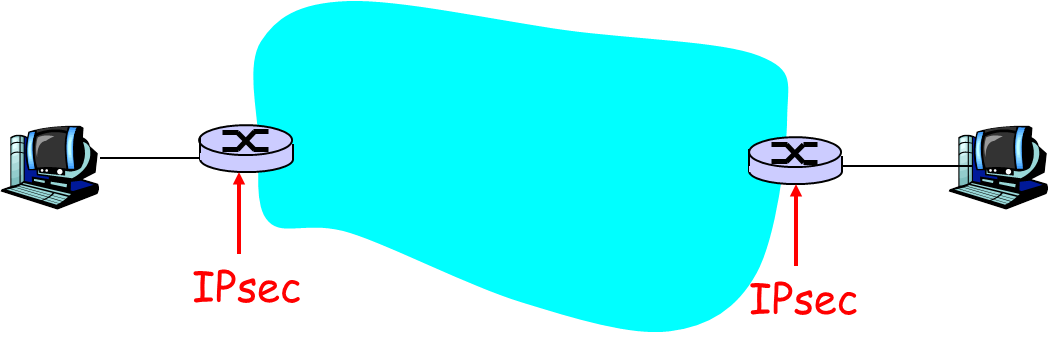
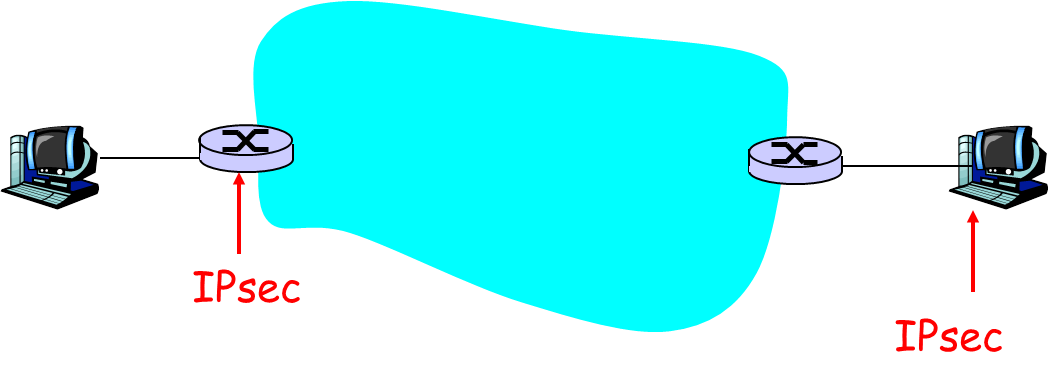
- Problem 3 [25pts] (IPSec)
- [6pts] We studied in the class that IPSec can be used in two different modes. Specify which of the two modes each of the figures below depict:
(a) [2pts] ___________________________

(b) [2pts] ___________________________
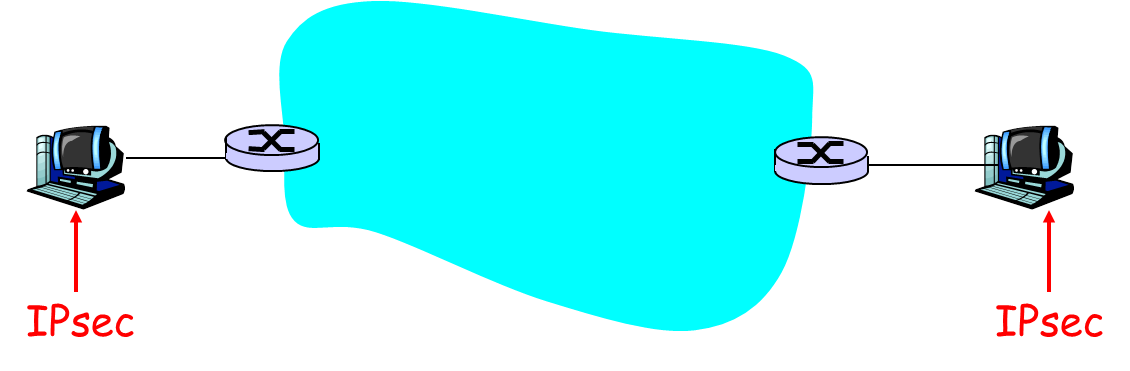
(c) [2pts] ___________________________
2[14=5+5+4pts] Explain the Diffie-Hellman Key exchange Is this protocol secure against a man-in-the-middle attacker? If not, show a man-in-the-middle attack, and explain how this attack can be fixed.
3.[2.5+2.5pts] Are the following statements True or False?
- IPSec can be used to protect both the payload and the header of a TCP packet.
- SSL/TLS can be used to protect both the payload and the header of a TCP packet.
Problem 4 [20pts] (Wireless Security)
- [5pts] Some wireless networks use white lists consisting of MAC addresses to prevent unauthorized users (wireless stations or hosts) from accessing the network. Is this a good defense? Why/why not?
- [5pts] Describe the encryption mechanism (both encryption and decryption procedures) that WEP employs to provide confidentiality of communication between a wireless host and a wireless AP (given that the two have a pre-shared symmetric key).
- [10pts] Assuming that WEP used only 32-bit long IVs, show an attack on the above encryption mechanism. That is, show how an attacker, who does not have access to the key shared between a host and an AP, can learn some communication between them (let’s say under a known-plaintext attack).
Problem 5 [30pts] (Required for 723 students. Optional for 423 and 623 students and can be done for extra points) 计算机final代考
In which order encryption and MAC are applied in IPSec? In which order encryption and MAC are applied in SSL?
Are these ordering mechanisms secure (please refer to and understand this paper to answer this question: http://www.iacr.org/archive/crypto2001/21390309.pdf

更多代写: HomeWork cs作业 金融代考 postgreSQL代写 IT assignment代写 统计代写 代写英国留学统计作业




发表回复
要发表评论,您必须先登录。